Deception Technology Market Opportunities, Strengths
Deception Technology 2024
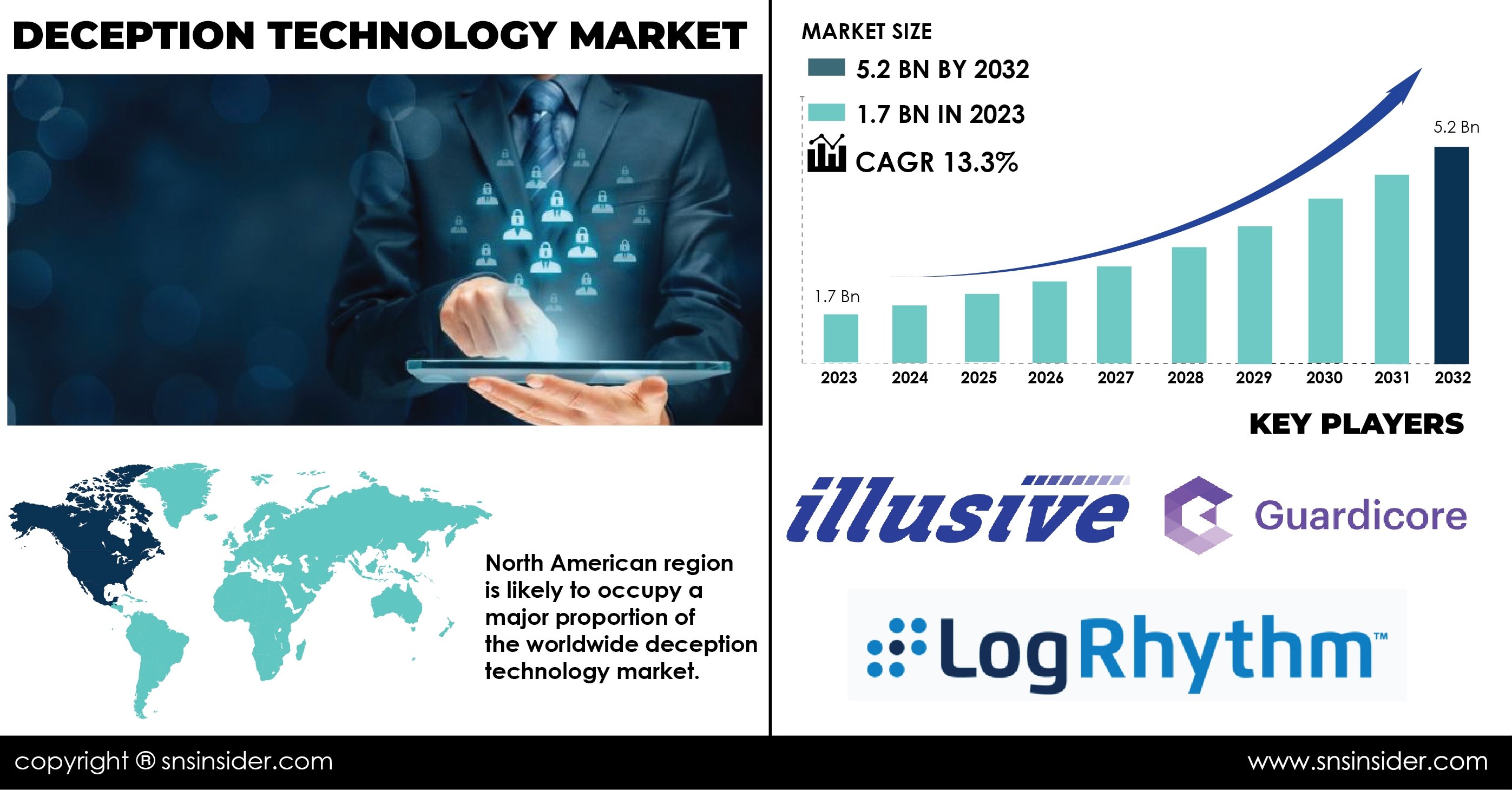
As cyber threats continue to evolve and become increasingly sophisticated, organizations are compelled to adopt innovative strategies to protect their sensitive data and infrastructure. One such approach gaining traction is deception technology, a proactive security measure designed to mislead attackers and divert them from valuable assets. By creating a virtual environment filled with fake data, systems, and assets, deception technology effectively tricks malicious actors into revealing their methods and intentions. This strategic approach not only enhances an organization's cybersecurity posture but also provides valuable insights for improving defenses. The Deception Technology Market Share reflects this growing trend, with the market size valued at USD 1.7 billion in 2023 and expected to grow to USD 5.2 billion by 2032, growing at a compound annual growth rate (CAGR) of 13.3% over the forecast period of 2024-2032.
Understanding Deception Technology
Deception technology operates on the principle of creating decoys, traps, and misleading data to confuse and misdirect potential attackers. This technology can manifest in various forms, including honeypots, which are traps set to lure attackers, and deceptive applications that mimic legitimate services. The core idea is to make the attacker believe they have successfully infiltrated a network while providing cybersecurity professionals with critical information about the attacker's tactics, techniques, and procedures (TTPs).
One of the fundamental components of deception technology is the ability to create an environment that appears legitimate. Organizations deploy various deceptive elements, such as fake databases, credentials, and servers, which can be indistinguishable from real assets. When attackers engage with these decoys, security teams can monitor their actions, identify vulnerabilities, and gather intelligence to enhance future defenses.
Benefits of Deception Technology
One of the primary advantages of deception technology is its ability to detect threats early. Traditional security measures, such as firewalls and intrusion detection systems, may not always catch sophisticated attacks until it is too late. In contrast, deception technology can quickly identify suspicious activity by monitoring interactions with deceptive assets. This early detection allows organizations to respond swiftly, potentially mitigating the impact of a security breach.
Moreover, deception technology enhances threat intelligence capabilities. By analyzing the behavior of attackers within the deceptive environment, security teams can gain insights into emerging threats and refine their overall security strategy. Understanding the methods attackers use allows organizations to strengthen their defenses and reduce their attack surface.
Another key benefit is the psychological impact on attackers. Knowing they might encounter deception can deter cybercriminals and force them to reconsider their tactics. In a world where attackers often target the weakest link, the presence of a deception technology framework can introduce uncertainty and discourage attempts to breach the network.
Furthermore, deception technology complements existing security measures. Rather than replacing traditional tools, it acts as an additional layer of defense. Organizations can integrate deception technology with their security operations to create a multi-faceted approach to cybersecurity. This synergy enhances the overall effectiveness of a security strategy by providing insights and intelligence that can inform incident response and threat hunting efforts.
Challenges and Considerations
Despite its many advantages, deception technology does present challenges that organizations must address. One significant concern is the potential for false positives. As deceptive elements can be mistaken for legitimate assets, security teams must ensure they can distinguish between real threats and benign interactions. Effective configuration and ongoing management of deceptive environments are critical to minimizing these false alerts.
Another challenge is resource allocation. Implementing and maintaining a deception technology framework requires dedicated resources, including personnel trained to analyze deceptive interactions and respond appropriately. Organizations must weigh the benefits of deception technology against the costs and resources required for its implementation.
Additionally, organizations must remain vigilant about the evolving tactics employed by cybercriminals. As attackers become more sophisticated, they may develop methods to identify and bypass deception technologies. Continuous adaptation and refinement of deceptive strategies are essential to staying ahead of potential threats.
Real-World Applications of Deception Technology
Deception technology is not limited to any specific industry; it is applicable across various sectors, including finance, healthcare, and government. Financial institutions, for instance, are frequent targets for cybercriminals seeking to exploit vulnerabilities for financial gain. By deploying deception technology, these organizations can protect sensitive customer data and transaction information from potential breaches.
In healthcare, where patient data is highly valuable, deception technology serves as a critical line of defense against data breaches. Hospitals and healthcare providers can implement deceptive elements to safeguard sensitive medical records, ensuring that patient information remains confidential and secure.
Government agencies also utilize deception technology to protect sensitive national security information. By employing decoys and traps, these agencies can identify potential threats to critical infrastructure and respond effectively to cyber espionage attempts.
The Future of Deception Technology
As the cyber threat landscape continues to evolve, deception technology is poised for growth and innovation. Advancements in artificial intelligence (AI) and machine learning (ML) are expected to enhance the effectiveness of deception strategies. By analyzing vast amounts of data and identifying patterns, AI and ML can help organizations optimize their deceptive environments and respond more effectively to threats.
The integration of deception technology with Security Information and Event Management (SIEM) systems is another promising development. Combining these technologies allows organizations to correlate deceptive interactions with broader security events, providing a comprehensive view of their security posture. This integrated approach enhances threat detection capabilities and streamlines incident response efforts.
Furthermore, the increasing demand for cybersecurity solutions among small and medium-sized enterprises (SMEs) presents new opportunities for deception technology. As these organizations seek affordable and effective security measures, providers of deception technology are likely to develop tailored solutions that meet their specific needs.
Conclusion
In conclusion, deception technology represents a significant advancement in the field of cybersecurity. By creating an environment that confuses and misleads potential attackers, organizations can enhance their security posture, detect threats early, and gather valuable intelligence to inform future defenses. The growing Deception Technology Market reflects the increasing recognition of its importance in safeguarding sensitive data and infrastructure. While challenges exist, the benefits of deception technology make it a valuable tool in the ongoing battle against cyber threats. As technology continues to evolve, organizations must stay ahead of the curve by integrating deception strategies into their broader security frameworks, ensuring a proactive approach to protecting their digital assets. Embracing deception technology is not just a reactive measure but a strategic investment in a more secure future.
Contact Us:
Akash Anand – Head of Business Development & Strategy
info@snsinsider.com
Phone: +1-415-230-0044 (US) | +91-7798602273 (IND)
About Us
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Read Our Other Reports:
Online Tutoring Services Market Trends
- Deception_Technology_Market
- Deception_Technology_Market_Size
- Deception_Technology_Market_Share
- Deception_Technology_Market_Growth
- Deception_Technology_Market_Trends
- Deception_Technology_Market_Report
- Deception_Technology_Market_Analysis
- Deception_Technology_Market_Forecast
- Deception_Technology_Industry
- Deception_Technology_Market_Research
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Games
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Other
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness


