5G Security Market Competitive Landscape, Growth Trends
5G Security 2024
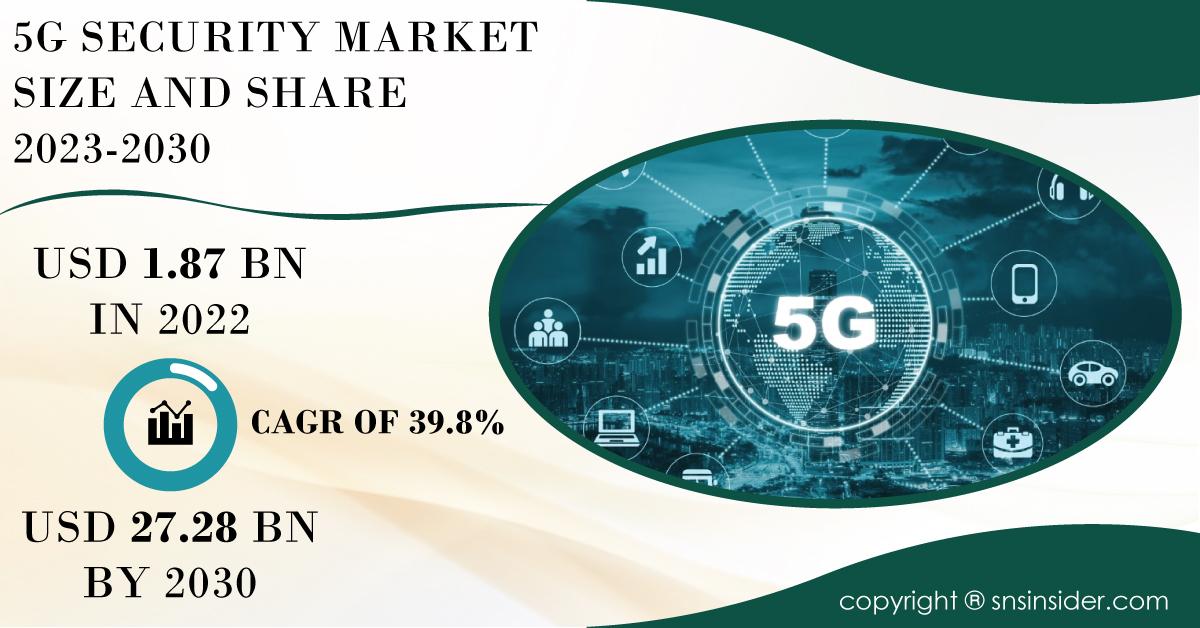
The advent of fifth-generation (5G) technology is set to revolutionize the way we connect and communicate. With its promise of significantly faster data speeds, reduced latency, and the ability to connect a massive number of devices, 5G will enable a plethora of new applications and services, including the Internet of Things (IoT), smart cities, autonomous vehicles, and enhanced mobile broadband. However, as the capabilities of 5G networks expand, so do the security challenges associated with them. The 5G Security Market Share is gaining traction, with a market size valued at USD 1.94 billion in 2023 and projected to grow to USD 26.42 billion by 2031, experiencing a remarkable compound annual growth rate (CAGR) of 38.6% over the forecast period of 2023-2030. This article delves into the security implications of 5G technology, the potential threats, the security measures being implemented, and the future of 5G security.
Understanding 5G Technology and Its Security Challenges
5G technology differs fundamentally from its predecessors, offering not only enhanced speed and capacity but also a more sophisticated architecture that integrates various technologies, including network slicing, edge computing, and virtualization. These advancements facilitate innovative use cases but also introduce new vulnerabilities.
One of the most significant challenges in securing 5G networks lies in their complexity. The shift from centralized to decentralized network structures means that security must be managed across multiple components and layers, including radio access networks (RAN), core networks, and transport networks. This intricate web of interconnected elements creates more points of potential failure and attack.
Moreover, the sheer volume of devices connected to 5G networks raises the stakes for security. With billions of IoT devices expected to operate on 5G networks, the attack surface expands exponentially. Many of these devices may lack robust security measures, making them attractive targets for cybercriminals. As more critical services and industries depend on 5G connectivity, the potential impact of security breaches escalates, prompting a pressing need for effective security measures.
Key Security Threats in 5G Networks
As with any technology, 5G networks are vulnerable to a range of security threats. One of the primary concerns is the risk of Distributed Denial of Service (DDoS) attacks. By overwhelming the network with traffic, attackers can render services unavailable, disrupting critical operations and causing significant financial losses. The ability of 5G to connect numerous devices simultaneously means that it is particularly susceptible to such attacks.
Another significant threat is the possibility of unauthorized access and identity theft. As 5G networks facilitate the use of numerous IoT devices, each with unique identities and credentials, ensuring that only authorized users can access network resources becomes increasingly challenging. Attackers may exploit vulnerabilities to gain unauthorized access, leading to data breaches and loss of sensitive information.
Additionally, the security of network slicing is a concern. Network slicing allows operators to create multiple virtual networks within a single physical infrastructure, each tailored to specific applications and use cases. While this offers flexibility and efficiency, it also raises the risk of vulnerabilities being exploited within one slice that could potentially impact others. Ensuring isolation and security across these slices is critical to maintaining the integrity of the overall network.
Furthermore, supply chain vulnerabilities pose a significant risk to 5G security. The complexity of 5G networks involves numerous vendors and components, making it challenging to ensure that all elements meet stringent security standards. Compromised hardware or software from any point in the supply chain can create backdoors for attackers, jeopardizing the entire network.
Security Measures for 5G Networks
To address these security challenges, a comprehensive and multi-layered approach is necessary. One key strategy is the implementation of end-to-end encryption. By encrypting data transmitted across the network, operators can safeguard sensitive information from interception and unauthorized access. End-to-end encryption ensures that even if data is compromised during transmission, it remains unreadable to potential attackers.
Another important measure is the deployment of advanced threat detection and response systems. These systems utilize artificial intelligence and machine learning algorithms to monitor network traffic for suspicious activity, enabling real-time detection and response to potential threats. By analyzing patterns and anomalies in data traffic, these systems can identify and mitigate threats before they escalate into significant security incidents.
Access controls also play a vital role in securing 5G networks. Implementing strict authentication and authorization measures ensures that only authorized users and devices can access network resources. Multi-factor authentication, role-based access controls, and continuous monitoring of user activities can significantly reduce the risk of unauthorized access.
Network slicing, while presenting unique security challenges, can also be fortified through dedicated security measures for each slice. This may include tailored access controls, monitoring, and encryption specific to the applications and users associated with each slice. By ensuring that vulnerabilities in one slice do not compromise the security of others, operators can maintain a robust security posture across the entire network.
Collaboration between stakeholders is crucial for enhancing 5G security. Mobile network operators, equipment manufacturers, regulatory bodies, and cybersecurity firms must work together to establish industry standards and best practices. By sharing threat intelligence and collaborating on security initiatives, the industry can better address emerging threats and vulnerabilities.
The Role of Regulations and Standards
As the adoption of 5G technology accelerates, regulatory bodies and industry organizations play a critical role in establishing security standards and guidelines. Governments around the world are recognizing the importance of cybersecurity in the context of 5G and are implementing regulations to ensure the integrity and security of networks.
For instance, the International Telecommunication Union (ITU) has developed a framework for security in 5G networks, focusing on risk management, incident response, and the implementation of best practices. Additionally, organizations such as the 3rd Generation Partnership Project (3GPP) are working on defining security requirements and protocols specifically tailored for 5G technology.
Regulatory frameworks that mandate security assessments, compliance audits, and vulnerability management can significantly enhance the overall security posture of 5G networks. By establishing clear expectations and guidelines, regulators can hold operators accountable for maintaining robust security practices.
The Future of 5G Security
Looking ahead, the landscape of 5G security will continue to evolve as technology advances and new threats emerge. The rise of artificial intelligence and machine learning will play a pivotal role in enhancing security measures. AI-driven systems will enable more sophisticated threat detection and response capabilities, allowing for proactive security measures that can adapt to evolving attack vectors.
Moreover, as the adoption of 5G technology expands, the focus on security will likely shift toward securing edge computing environments. With the increasing reliance on edge computing for processing data closer to the source, securing these environments will become paramount. Ensuring that edge devices are adequately protected against threats will be critical to maintaining the overall security of 5G networks.
Collaboration and information sharing among industry stakeholders will remain essential for addressing emerging threats. As cybercriminals become more sophisticated, sharing threat intelligence and best practices will enable the industry to stay one step ahead of potential attacks. Furthermore, continuous training and awareness programs for employees and stakeholders will be vital for fostering a culture of security.
Conclusion
As 5G technology reshapes the connectivity landscape, the importance of robust security measures cannot be overstated. The rapid expansion of 5G networks brings both tremendous opportunities and significant challenges in terms of security. The 5G Security Market is poised for substantial growth, reflecting the increasing emphasis on safeguarding these critical infrastructures. By adopting a comprehensive approach that includes encryption, advanced threat detection, access controls, and collaboration among stakeholders, the industry can mitigate the risks associated with 5G technology. As we move forward, the commitment to securing 5G networks will be essential in ensuring that this transformative technology fulfills its potential while safeguarding users and businesses alike.
Contact Us:
Akash Anand – Head of Business Development & Strategy
info@snsinsider.com
Phone: +1-415-230-0044 (US) | +91-7798602273 (IND)
About Us
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Read Our Other Reports:
Public Key Infrastructure (PKI) Market Growth
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Juegos
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Other
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness


